Strong Cyber Security, Privacy & AI Governance — ready in weeks, using your existing systems, at a significantly lower cost.
Strong product. Strong pipeline. Still losing revenue because compliance proof can't be delivered fast and credibly.
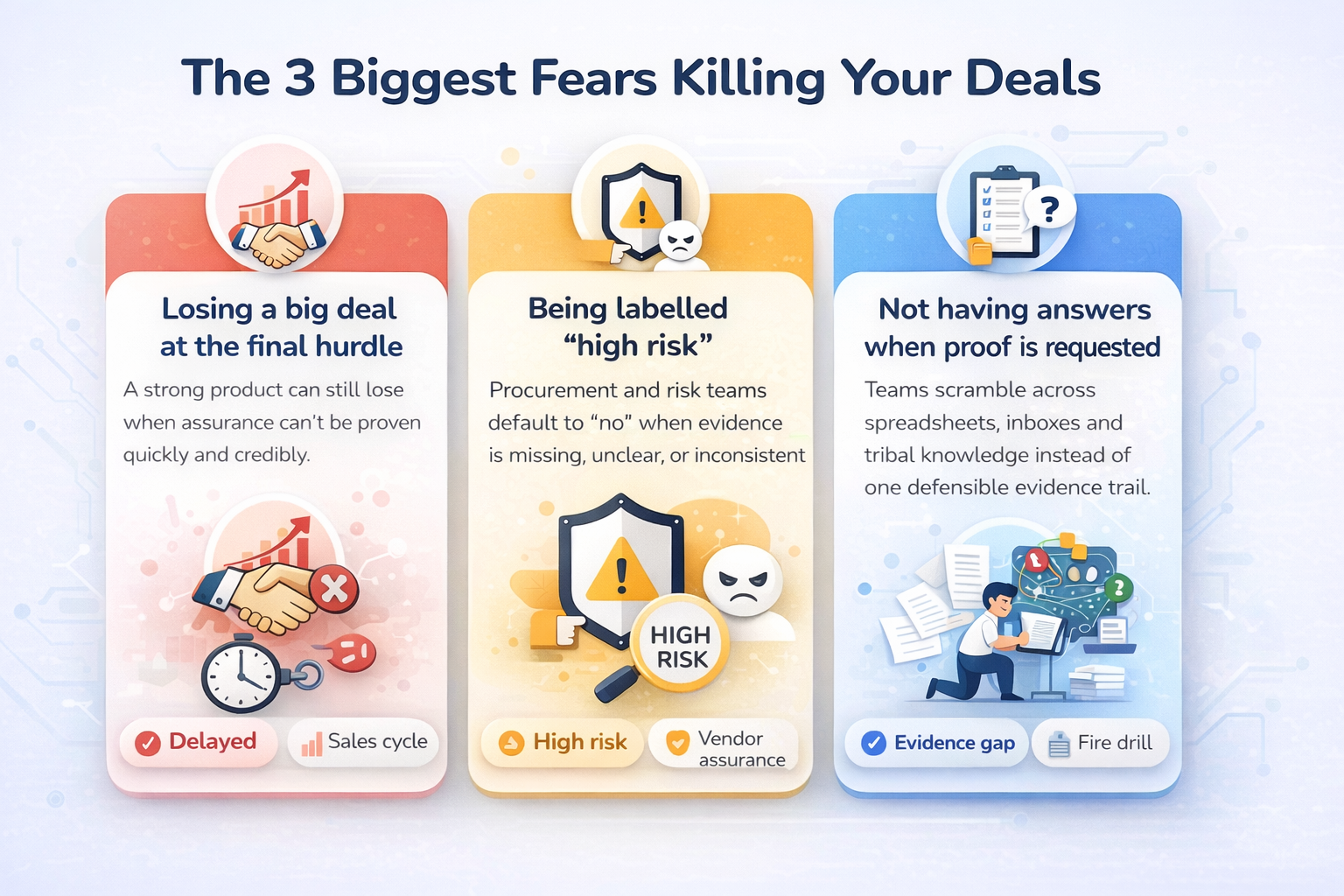
Confidence. Speed. Evidence. Calm teams — not chaos.
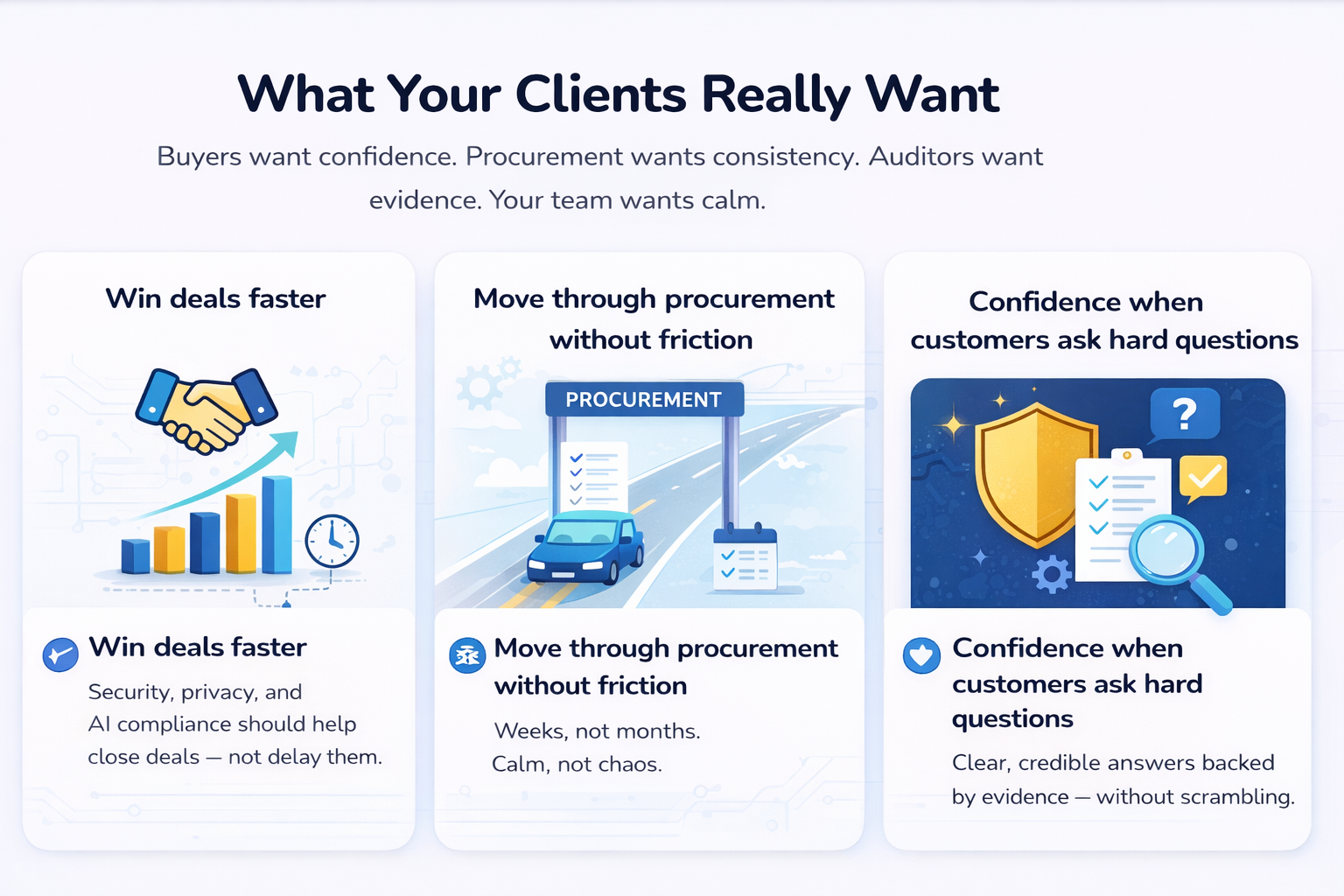
Security, privacy & AI compliance should shorten sales cycles — not extend them. Turn blockers into your competitive advantage and accelerate pipeline velocity.
Weeks, not months. Predictable timelines. Defensible evidence that lets procurement confidently approve — without delays or risk flags.
Deliver auditor-ready, customer-trusted answers in minutes — no last-minute scrambles, no credibility gaps. Reusable proof that builds trust at scale.
Stop wasting time and budget on outdated methods. See how we deliver faster, cleaner results that accelerate revenue — not slow it down.
Trusted by SaaS and tech teams that need compliance to accelerate growth — not slow it down.
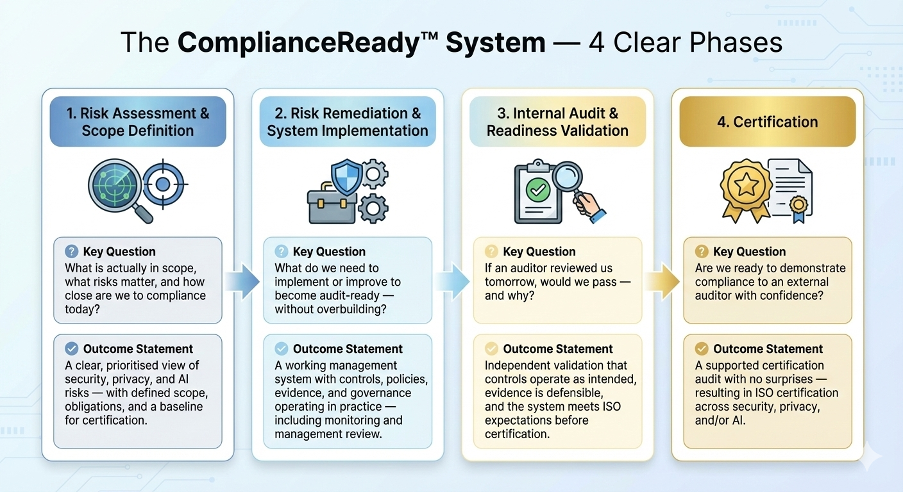
Get Compliant & Win Deals FasterStructured, fast, and completely inside your existing environment — no new tools, no extra licenses, no disruption.
We map exactly what’s in scope, identify real risks that matter, and define a clear, prioritized baseline — all using your current Microsoft 365 / existing stack.
Targeted, minimal remediation — we build controls, policies, workflows, and automated evidence capture directly inside your environment.
Independent review to confirm: If an auditor walked in tomorrow, would we pass? We validate evidence traceability and produce a clean audit pack.
Full support through external certification — assessor Q&A, final evidence packaging, and a calm, surprise-free audit experience.
We get these questions a lot. Here are the answers that matter most to fast-moving SaaS and tech teams.
No. Everything is built directly inside your existing environment (Microsoft 365, SharePoint, etc.). No new tools, no forced change management, no endless meetings. Your team stays focused on building product.
We typically deliver audit-ready compliance in 8–12 weeks (depending on scope). Most teams see significant progress in the first 4 weeks. Compare that to the 6–18 months traditional consultants often take.
A fraction of large consulting firms or GRC tool subscriptions — usually 60–80% less. Fixed pricing with no hidden fees or scope creep. We align cost to real business value, not hours billed.
ISO 27001, ISO 27701 (Privacy), ISO 42001 (AI Governance), SOC 2, Essential Eight, DISP/ISM/IRAP, NIST CSF — and mappings between them. One set of controls, multiple certifications.
Still have questions? We’re happy to answer them.
Book a Free CallWeeks average to audit-ready
Inside existing environments
Certification/surveillance passed
Book a free 30-minute call — we'll show you how to get audit-ready fast, close more deals, and avoid months of delays.
Limited spots available — most teams see results in under 4 weeks.